Are your printed documents being tracked without your knowledge? The answer might surprise you. In an effort to combat counterfeiting, some color laser printer manufacturers have agreed to encode each page with identifying information, potentially allowing for print tracking and surveillance.
This technology has raised concerns about privacy violations and government abuse. The American Civil Liberties Union (ACLU) has voiced their worries and highlighted the lack of regulations to protect individuals from unwanted surveillance.
Join us as we delve into the controversial world of print tracking, uncovering the truth behind printer surveillance and document tracing. In this article, we'll explore the use of secret printer codes, examine the role of microdots in FBI investigations, discuss steganography and hidden messages, explore risks associated with printing and scanning, and shed light on the debate surrounding printer tracking technology.
Key Takeaways:
- Color laser printers may encode identifying information on each page, potentially allowing for print tracking and surveillance.
- The lack of regulations leaves room for government agencies to use these codes for surveillance purposes, raising concerns about privacy violations.
- Microdots, tiny coded designs on printed documents, have been used in high-profile FBI cases, sparking interest in their tracking potential.
- Steganography techniques, such as hidden messages, can leave trails on printed documents, potentially compromising privacy.
- Printing and scanning documents pose risks to data security, including malware infections and traces left on external storage media.
The Controversial Use of Printer Codes
The use of secret printer codes on printed documents has raised concerns about government surveillance and potential privacy violations. Color laser printer manufacturers have been pressured by the US government to include identifying information on each page in order to aid in the detection of counterfeiters.
While the intention behind these printer codes is to combat counterfeiting, the lack of regulations surrounding their use has raised significant concerns. There are currently no laws in place to prevent government agencies, such as the Secret Service, from utilizing these codes for surveillance purposes.
This lack of oversight leaves the door open for potential privacy violations, as the encoded information on printed documents can potentially be used to track individuals without their knowledge or consent. The inclusion of these secret codes on printed documents poses ethical questions and raises concerns about the extent of government surveillance.
“The use of printer codes without proper regulations can lead to privacy violations and potential abuse by government agencies.” – Privacy Advocate
It is essential to address these concerns and establish clear guidelines to protect individuals' privacy rights while maintaining efforts to combat counterfeiting. Striking a balance between maintaining security measures and respecting personal privacy is crucial in the digital age.
Examples of Secret Printer Codes:
Here are some examples of the types of information that can be encoded in printer codes:
| Encoded Information | Purpose |
|---|---|
| Printer Serial Number | Linking printed documents to specific printers |
| Print Timestamp | Tracking the date and time of the printout |
| Printer Model | Identifying the type of printer used |
These examples provide a glimpse into the potential capabilities and implications of printer codes. The use of such codes raises legitimate concerns about privacy and the extent of government surveillance.
With the advancement of technology, it is important to have a thorough understanding of the implications associated with the use of secret printer codes. This ongoing debate highlights the need for comprehensive regulations that protect individuals' privacy rights while addressing the concerns of law enforcement agencies.
The FBI Case and Microdots
In a high-profile FBI investigation, the discovery of microdots on a leaked document has sparked significant interest in their potential as a tracking tool. Microdots are incredibly small and nearly invisible to the naked eye. These tiny dots contain a coded design that reveals the precise date and time the pages were printed. Additionally, they encode a unique serial number specific to the printer used.
While it remains unclear whether the microdots were instrumental in identifying the suspect in this particular case, their presence has raised questions about their effectiveness as a forensic tool. The ability to track and trace printed documents through microdots presents intriguing possibilities for law enforcement agencies.
“The presence of microdots on the leaked document certainly piques our interest. These dots could potentially serve as crucial evidence in identifying individuals involved in sensitive leaks or criminal activities.” – FBI spokesperson.
The Power of Microdots
Microdots function as covert markers that leave subtle traces on documents, providing valuable information about their origins and the printing apparatus used. With their ability to encode data in a minuscule format, microdots offer a discreet means of establishing document authenticity and tracing their source.
- Identification: The unique serial number embedded within microdots can help identify the specific printer used, facilitating the investigation process and eliminating false leads.
- Forensic Analysis: By analyzing the encoded design, investigators can determine when and where the document was printed. This information can be crucial in establishing the timeline of events.
- Case Linkage: Microdots may potentially connect different printed documents to a common source or printer, aiding in the identification of individuals involved in criminal activities or leaks.
Intriguingly, microdots go beyond traditional methods of document tracking and provide law enforcement agencies with an additional layer of evidence in complex investigations.
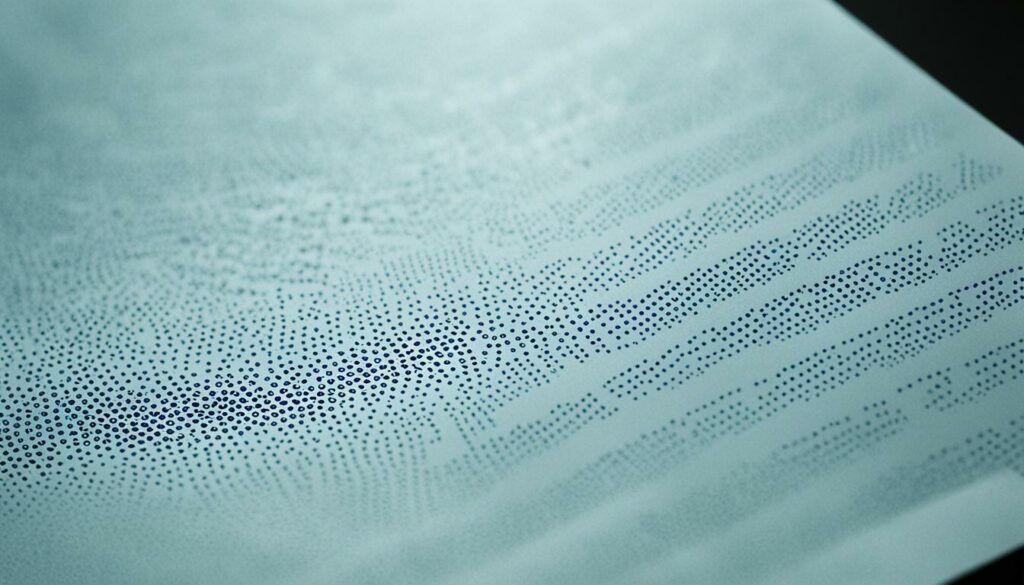
The Potential Ethical Concerns
The utilization of microdots raises valid ethical concerns regarding privacy and personal identification. While these dots enhance investigations by making document tracing more efficient, their presence on printed materials can infringe upon personal privacy rights. Striking a balance between effective law enforcement and safeguarding civil liberties remains at the forefront of discussions surrounding the use of microdots.
| Pros | Cons |
|---|---|
| Enhanced document traceability | Potential invasion of privacy |
| Facilitates investigation process | Raises ethical concerns |
| Supports the fight against counterfeiting and leaks | Requires careful balance between law enforcement and privacy |
Steganography and Hidden Messages
Steganography, the art of hiding secret messages in plain sight, has a long history. This technique involves concealing information within ordinary-looking objects or media, making it difficult to detect by unintended recipients or monitoring systems.
An intriguing example of steganography is the Eurion constellation pattern found on many banknotes worldwide. Designed to prevent counterfeiting, this pattern consists of a series of small circles that can be recognized by image-processing software. By embedding this hidden feature, authorities can easily differentiate genuine banknotes from counterfeit ones.

“The beauty of steganography lies in its ability to mask information within seemingly innocuous forms. It's like hiding a needle in a haystack, making it nearly impossible for prying eyes to even suspect the presence of hidden messages.” – Dr. Olivia Richards, Cybersecurity Expert
During World War Two, German spies utilized tiny steganographic dots on documents to covertly transmit information. These dots, each no larger than a printed period, contained coded messages that only knowledgeable individuals could decipher. Being virtually indistinguishable from regular ink dots, they played a crucial role in secret communications among agents.
Modern steganography techniques have evolved to incorporate digital mediums. One method involves encoding invisible messages within trailing whitespace. By appending hidden information at the end of a text file, it is possible to create covert channels for communication.
While steganography enables covert communication, it is important to note that these techniques leave identifying trails on documents. Analyzing the patterns, structures, or unusual characteristics of a file can reveal the presence of hidden messages. As such, it is crucial to consider the potential risks and implications of steganography in the context of data privacy and security.
Examples of Steganography Techniques:
- Text-based steganography: Concealing information within text files, leveraging techniques such as whitespace manipulation or modifying word spacing.
- Image steganography: Embedding hidden messages within images by subtly altering the color or pixel values, using techniques like LSB (least significant bit) substitution.
- Audio steganography: Hiding confidential data within audio files by imperceptibly modifying the audio waveform or perceptual audio coding.
Steganography continues to be an intriguing field of study, highlighting the ingenious and creative ways individuals aim to maintain secrecy in the digital era. However, it also raises important considerations regarding privacy, security, and the potential misuse of hidden communication methods.
Risks Associated with Printing and Scanning
When it comes to printing and scanning documents, there are important risks to consider in terms of data security. These processes involve the use of computers and devices that may be vulnerable to malware, compromising sensitive information. Additionally, log files and traces left on external storage media can potentially reveal valuable insights about the devices and individuals involved. To mitigate these risks, it is crucial to take appropriate precautions, such as utilizing secure operating systems and secure storage media.
Mitigating Malware Risks
Malware, a significant threat to data security, can infiltrate computers and devices during the printing and scanning processes. It can spread through connected storage media, infecting other systems and compromising sensitive information. To safeguard against these risks, it is essential to:
- Ensure devices have up-to-date antivirus software installed.
- Regularly scan devices for malware and other malicious programs.
- Exercise caution when connecting external storage media, such as USB drives or memory cards, to printing or scanning devices.
- Only use trusted and secure storage media to minimize the risk of malware transmission.
Protecting Against Data Leakage
Log files and traces left on external storage media can potentially reveal information about the devices used for printing and scanning, as well as the individuals involved. These traces can be accessed through digital forensics techniques, posing a risk to data privacy and security. To protect against potential data leakage, it is crucial to:
- Regularly clear log files and traces from external storage media used for printing and scanning.
- Encrypt sensitive data to prevent unauthorized access.
- Consider using secure storage media with built-in encryption features.
- Dispose of external storage media securely, ensuring data is irrecoverable.

Ensuring data security in the printing and scanning processes is essential to preserve privacy and protect sensitive information. By staying vigilant and implementing the necessary precautions, individuals and organizations can mitigate the risks associated with malware, data leakage, and digital forensics.
Privacy Considerations and Storage Media
When it comes to printing and scanning documents, privacy is a top concern. Using external storage media, such as USB sticks or cell phones, can leave traces and information that could potentially identify the person responsible for the document. This highlights the need for proper data logging and secure storage methods to protect sensitive information.
Traceable Information on External Storage Media
Log files on external storage devices can contain valuable information, including hardware serial numbers and product names. This data can potentially be used to identify the device and the individual associated with the printed or scanned document. To avoid this, it is crucial to use operating systems that do not log this information, or securely delete any log files stored on the external storage media.
Secure Storage Media for Privacy Protection
Choosing secure storage media is essential for safeguarding privacy. By using encrypted USB drives or secure cell phones, you can ensure that the data stored on these devices remains inaccessible to unauthorized individuals. In addition, securely destroying storage media that is no longer needed can prevent any potential data breaches or identification of the person responsible for the document.

| External Storage Media | Privacy Considerations |
|---|---|
| USB Sticks | Traces of log files containing hardware serial numbers, product names, and other identifiable information. |
| Cell Phones | Potential identification of the device and the individual responsible for the document. |
By being mindful of data logging and using secure storage methods, individuals can protect their privacy during the printing and scanning process. Awareness and proactive measures are key to maintaining the confidentiality of sensitive information.
Data Storage on Multi-Function Printers
Multi-function printers are equipped with internal storage devices, such as hard disks, to store firmware, settings, and data for printing, copying, and scanning. This storage can contain a wealth of sensitive information, including actual data and management information.
However, it's crucial to recognize that this data can potentially be recovered if not properly erased. To ensure data security and prevent unauthorized access, it is important to implement appropriate measures for data erasure.
“Proper data erasure on multi-function printers is essential to protect sensitive information and maintain data security.”
One effective method of data erasure is overwriting the stored data according to industry standards. For instance, the Department of Defense (DoD) standard provides a comprehensive and secure approach to overwrite data to mitigate the risk of data recovery.
Additionally, periodically resetting the devices to factory settings can further ensure that any residual data or configurations are effectively erased.
In cases when storage devices are no longer needed or have reached the end of their lifecycle, it is recommended to physically destroy the devices to prevent any potential data breaches or recovery attempts.
To summarize, proper data erasure on multi-function printers is crucial for maintaining data security and preventing unauthorized access to sensitive information. By following industry-standard practices and regularly resetting devices, individuals and organizations can protect their data and mitigate the risk of data breaches.
Best Practices for Data Erasure on Multi-Function Printers
- Follow industry-standard data erasure methods, such as the DoD standard.
- Periodically reset devices to factory settings to remove residual data and configurations.
- Physically destroy storage devices that are no longer needed or have reached the end of their lifecycle.
| Storage Device | Data Erasure Method | Security Level |
|---|---|---|
| Hard Disk Drive (HDD) | Overwriting with random data multiple times | High |
| Solid State Drive (SSD) | Encryption and secure erase commands | High |
| Print Job Logs | Clearing logs and resetting to factory settings | Medium |
Misprints and Forgotten Documents
Misprints and forgotten documents can pose risks to data protection. Proper disposal of sensitive documents is crucial to protecting data privacy. Here are some important considerations:
Shredding Misprints
Shredding misprints directly into small particles using document shredders can ensure that the information cannot be pieced back together. By reducing misprints to confetti-like fragments, the risk of unauthorized access to sensitive data is significantly minimized.
Handling Forgotten Documents with Care
Forgotten documents should be handled with care to prevent unauthorized access and potential data breaches. Important originals should be retained securely, while obvious copies and printouts should be securely destroyed to avoid any possible misuse of sensitive information.
“Proper disposal of sensitive documents is crucial to protecting data privacy.”
Document Disposal Best Practices
When disposing of sensitive documents, it is important to follow best practices to ensure data protection. Consider the following:
- Use document shredding services: When dealing with large quantities of sensitive documents, utilizing professional document shredding services can provide secure disposal and peace of mind.
- Invest in a reliable document shredder: For smaller-scale document disposal needs, investing in a reliable document shredder can be a cost-effective solution. Look for shredders that cross-cut or micro-cut paper for enhanced security.
- Implement a document destruction policy: Establishing a documented policy for document disposal within your organization can help ensure that all employees are aware of the proper procedures to follow.
By incorporating these practices into your data protection strategy, you can mitigate the risks associated with misprints and forgotten documents, safeguarding sensitive information from unauthorized access.
| Benefits of Document Shredding | Benefits of Document Disposal Policy |
|---|---|
| Prevents unauthorized access to sensitive information | Ensures consistent and secure disposal practices |
| Protects against identity theft and fraud | Raises awareness among employees about data privacy |
| Complies with data protection regulations | Reduces the risk of data breaches |
Proper document disposal is a crucial aspect of data protection. By prioritizing secure disposal methods, you can minimize the risks associated with misprints and forgotten documents, safeguarding sensitive information and preserving data privacy.

Traces on Printouts and Scanned Documents
Printouts and scanned documents can contain traces that reveal information about the printer, device, and person responsible for the document. These traces, often in the form of machine identification codes, can have implications for print traceability and privacy. It is crucial to understand the presence of these traces and the potential privacy concerns they raise.
Machine Identification Codes, also known as tracking dots or microdots, are embedded in printouts and scanned documents. These codes encode identifying information such as serial numbers and print timestamps. While they may not be visible to the naked eye, they can be detected using specialized equipment or software.
Machine identification codes are utilized by various entities, including law enforcement agencies and security organizations, to track the source of documents and identify individuals involved in leaks or counterfeiting. These codes have been effective in investigations, providing valuable evidence in cases involving document leaks and counterfeit operations.
The use of machine identification codes raises important questions about privacy and the potential for surveillance. While they serve a legitimate purpose in criminal investigations, their presence on ordinary documents can be seen as an invasion of privacy. It is essential to strike a balance between law enforcement needs and individual privacy rights.
Examples of Machine Identification Codes:
| Code Type | Description |
|---|---|
| Serial Number Code | Encodes the unique serial number of the printer or scanner used |
| Timestamp Code | Indicates the date and time the document was printed or scanned |
| Signature Code | Includes a unique pattern that can be used to identify the specific printer model |
While machine identification codes can be concerning from a privacy standpoint, it is important to note that not all printers and scanners use these codes. Some manufacturers have chosen not to include them in their devices, prioritizing user privacy. However, it is recommended to be cautious and aware of the potential presence of these codes, especially when handling sensitive or confidential documents.
![]()
The Debate Over Printer Tracking Technology
The use of printer tracking technology has sparked a heated debate surrounding privacy concerns and potential human rights violations. Critics argue that the inclusion of identifying information on printed documents, without the knowledge or consent of individuals, constitutes a significant breach of privacy. This controversial practice has led to widespread dissatisfaction and numerous printer complaints.
Organizations like the Electronic Frontier Foundation (EFF) have been at the forefront of raising awareness about the privacy implications of printer tracking technology. They have voiced their concerns and received thousands of complaints from individuals who believe that their privacy rights are being compromised.
“The inclusion of identifying information on printed documents without informed consent represents a serious violation of privacy rights. It is imperative that individuals have control over the information they share and the knowledge of how it is being used.” – Electronic Frontier Foundation
The ethical implications of printer tracking technology continue to be a topic of discussion among policymakers, privacy advocates, and the public. The potential invasion of privacy and the impact on human rights have raised questions about the legality and necessity of such practices.
The Importance of Privacy
- Protecting individuals' privacy is essential in upholding human rights and ensuring personal freedom.
- Privacy allows individuals to maintain control over their personal information and make informed decisions about how it is shared or used.
- The robust protection of privacy is necessary to prevent potential abuses of power and protect against unauthorized surveillance or monitoring.
The Need for Transparency and Consent
- Printer users should have clear and accessible information about any tracking or surveillance capabilities embedded in their devices.
- Informed consent should be obtained from individuals before activating any tracking or identification features.
- Transparency and user control can help strike a balance between the legitimate need to combat counterfeiters and the protection of individual privacy rights.

The Impact on Society
- Printer tracking technology has the potential to erode trust in institutions and hinder intellectual freedom.
- The constant surveillance of printed materials can create a chilling effect, discouraging the free exchange of ideas and information.
- The existence of surveillance practices without proper safeguards can compromise individuals' rights to privacy and freedom of expression.
Addressing Privacy Concerns
The debate surrounding printer tracking technology highlights the urgent need for comprehensive privacy regulations. Stricter laws and transparency requirements can ensure that individuals' privacy rights are respected.
By taking steps to address privacy concerns and advocate for stronger legal protections, individuals and organizations can contribute to safeguarding human rights and protecting against potential privacy violations.
Conclusion
The use of printer tracking technology raises significant concerns about data privacy and personal identification. With the inclusion of machine identification codes and other tracking methods, individuals are at risk of compromising their privacy and enabling surveillance.
Currently, there are limited regulations in place to protect against these risks. It is essential for individuals to be aware of the potential dangers associated with printing and scanning documents and to take necessary precautions to safeguard their privacy.
To enhance data privacy, it is advisable to use secure operating systems that prioritize protection. Additionally, securely disposing of sensitive documents can prevent unauthorized access to personal information. It is equally important to be mindful of the information embedded in printouts and to exercise caution when handling and sharing documents.
As the digital world continues to evolve, protecting data privacy and personal identification becomes increasingly crucial. By adopting secure practices and staying informed about the potential risks, individuals can navigate the world of printing and scanning with greater confidence and peace of mind.

I'm Morgan, the creator of VPNForMe — a site born from too many hours spent side-eyeing sketchy VPN reviews and buffering videos.
I wanted a place where people could get straight answers about privacy, streaming access, and which VPNs actually deliver — without the hype or tech jargon.

